Ransomware Detection 101
This article explains Datto's process for detecting ransomware and what you should do if you suspect a machine has ransomware.
Environment
- Datto SIRIS
- Datto ALTO
Description
What is Datto Ransomware Detection?
Datto Ransomware Detection is available to protected Windows machines using the Datto Windows Agent or Agenless solution and is enabled by default. Datto designed Ransomware Detection to check for suspicious file patterns that resemble ransomware activity. With the alert, you can immediately take action and determine if there is indeed a problem. The results can then be used to improve Ransomware Detection.
Explaining Ransomware Detection and false-positives
Datto's Ransomware Detection works by detecting patterns of change in specific file types, rather than analyzing specific files. For example, it's highly unlikely that a user or legitimate program would rapidly and simultaneously:
- Perform an in-place file content overwrite with random data.
- Overwrite the content of ONLY the file types that ransomware commonly targets.
- Exclude file types commonly ignored by ransomware.
- Preserve all the original file modified timestamps, including overwritten files.
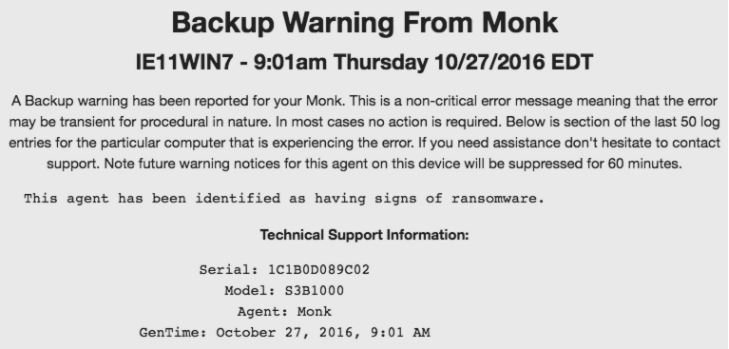
In a case like this, the Datto device would create an alert for suspected ransomware infection.
Ransomware alerts may sometimes be false-positives if a legitimate program uncharacteristically updates files.
If a particular agent persistently false-alerts for ransomware (with no apparent infection), you can disable detection for that agent from the Configure Agent Settings page of the Datto appliance. You should only do this as a last resort.
IMPORTANT Disabling Ransomware Detection for a protected system will also disable all historical infection reporting for that system until you re-enable the feature.
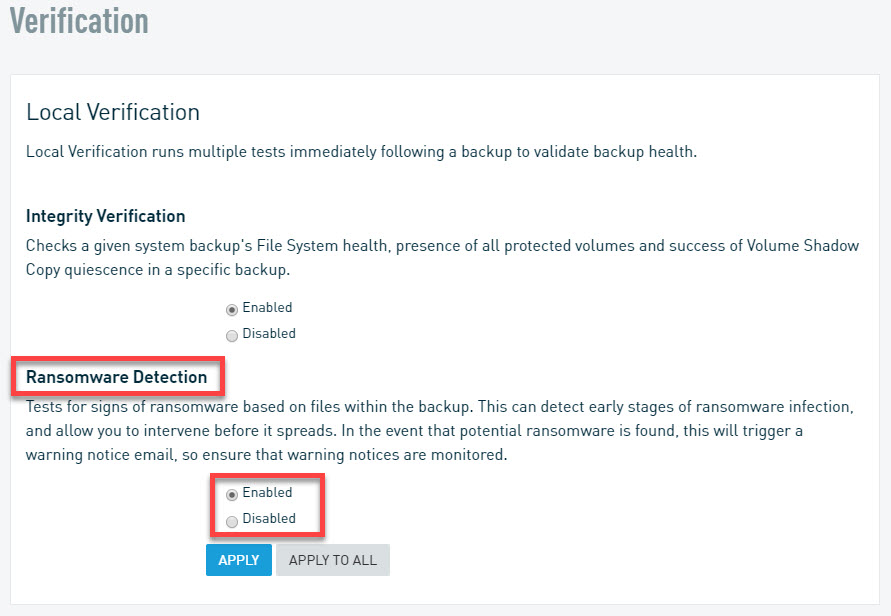
Your Datto appliance enables Ransomware Detection by default. You can enable or disable this feature for each protected system individually in the Datto web UI by clicking Protect > Configure Agent Settings (or Configure System Settings). You'll see Ransomware Detection listed under the Verification section.
Steps for finding ransomware
If you suspect ransomware infection, there are several steps you can take:
- Boot the device or access it remotely. Often infected machines will boot with a window telling you who to contact and how long you have. If you don't have remote access to the server or don't want to connect to it or interrupt end users, you have two other options:
- Start a virtualization of the impacted server on your Datto appliance and browse the root folders of the OS volume
- Create a file restore from the Datto appliance GUI and review the file extensions within it. Files with extensions such as .ecc, .ezz, .exx, .zzz, .xyz, .aaa, .abc, .ccc, .vvv, .xxx, .ttt, .micro, .encrypted, .locked, .crypto, .cryptowall, _crypt, .cryp1, .zepto, .crinf, .r5a, .XRNT, .XTBL, .crypt, .R16M01D05, .pzdc, .good, .LOL!, .OMG!, .RDM, .RRK, .encryptedRSA, .crjoker, .EnCiPhErEd, .LeChiffre, .keybtc@inbox_com, .0x0, .bleep, .1999, .vault, .HA3, .toxcrypt, .magic, .SUPERCRYPT, .CTBL, .CTB2, .locky, .fun, or 6 - 7 character long extensions consisting of random numbers, letters, and symbols.may have been infected with ransomware.
- Open either Microsoft Word or Excel, and see if those applications display any error or warning. Office and Word files are common targets of infections.
- Inspect common document folders, such as My Documents. See if file names or extensions are changing or if recent files have disappeared. Pay particular attention to .doc, .docx, .jpg, .xlsx, .pptx and similar common personal file types.
- Determine if any other local software behaves similarly to ransomware. For example, Dropbox encrypts local files in a way that resembles the random file encryption of ransomware.
- Log into file sync and share platforms. Often file sync and share applications propagate all file changes, which can include ransomware. Log in to the web interface of the file sync and share solution connected to the suspect system and inspect files. Altered file names or extensions will often appear.
- Use the antivirus and anti-malware software on your production machine to check for an infection. Address any threats detected.
Next steps
If you do find actual ransomware on the machine, dont panic. Dattos Data Continuity solutions are built to restore the machine to a time before the attack took place. See What to do if a protected machine is infected with ransomware for steps you can use to recover.