Connecting a SIRIS to a Hyper-V Hypervisor
This article describes how to connect a Datto SIRIS to a Hyper-V hypervisor. These instructions apply to virtual and physical SIRIS appliances.
For vSphere instructions, see Virtualize via Hypervisor for VMware environments.
Environment
- Datto SIRIS
- Microsoft Hyper-V
- Windows Server 2012 R2
- Windows Server 2016
- Windows Server 2019
- Windows Server 2022
- Windows Server 2025
Description
Datto SIRIS appliances can establish connections to Hyper-V environments to offload screenshot and disaster recovery virtualizations to the hypervisor. This connection allows the virtualizations to take advantage of the expanded system resources available on the Hyper-V host, delivering increased virtual machine performance, while decreasing overhead on your Datto appliance.
NOTE Datto SIRIS does not support taking agentless backups through the Hyper-V connection. Support for agentless pairings is limited to VMware environments only.
Technical Notes
- The platforms listed in the Environment field of this article all support Hyper-V integration.
- SIRIS Hyper-V virtualizations are Hyper-V Generation 1 virtual machines.
- SIRIS shares out backup images for Hyper-V restores via iSCSI.
- Datto appliances do not currently support Hyper-V Shared Live Migration.
- iSCSI targets containing underscores (such as backup_device) are not supported.
- Virtualizations and screenshots offloaded to Hyper-V rely on virtual IDE controllers, which limits virtualizations to the boot volume and a maximum of three attached disks.
- To prevent blocked connection attempts between your Datto appliance and the target hypervisor, create any necessary network exceptions in your antivirus and firewall solutions before attempting this procedure.
- To prevent blocked connection attempts between your Datto appliance and the protected system, if your hypervisor is using anti-virus or anti-malware software, you will also need to create an exception for %systemdrive%\Windows\winexesvc.exe
Configuring Hyper-V
If you are setting up a Virtual SIRIS on Hyper-V that has been deployed through Datto RMM, firewall rules and winrm commands will have already been configured. You can skip to the Setting up the Hypervisor Connection section of the article.
Depending on the configuration of your Hyper-V host, you may need to make changes to allow your SIRIS to connect to the hypervisor. If following the steps do not result in a successful hypervisor connection, follow the steps in the Enabling and configuring winrm and Windows Firewall section.
Enabling this rule in Windows Firewall will allow your SIRIS to connect and create a hypervisor connection for screenshots and hypervisor virtualizations:
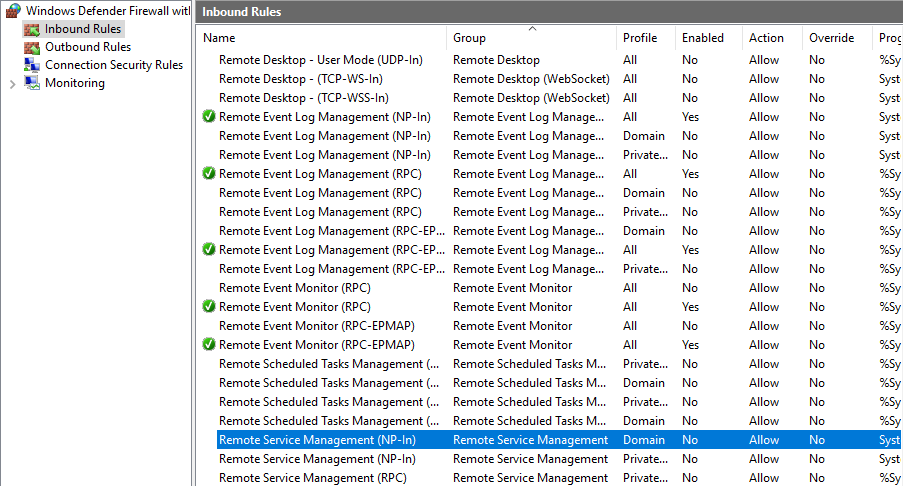
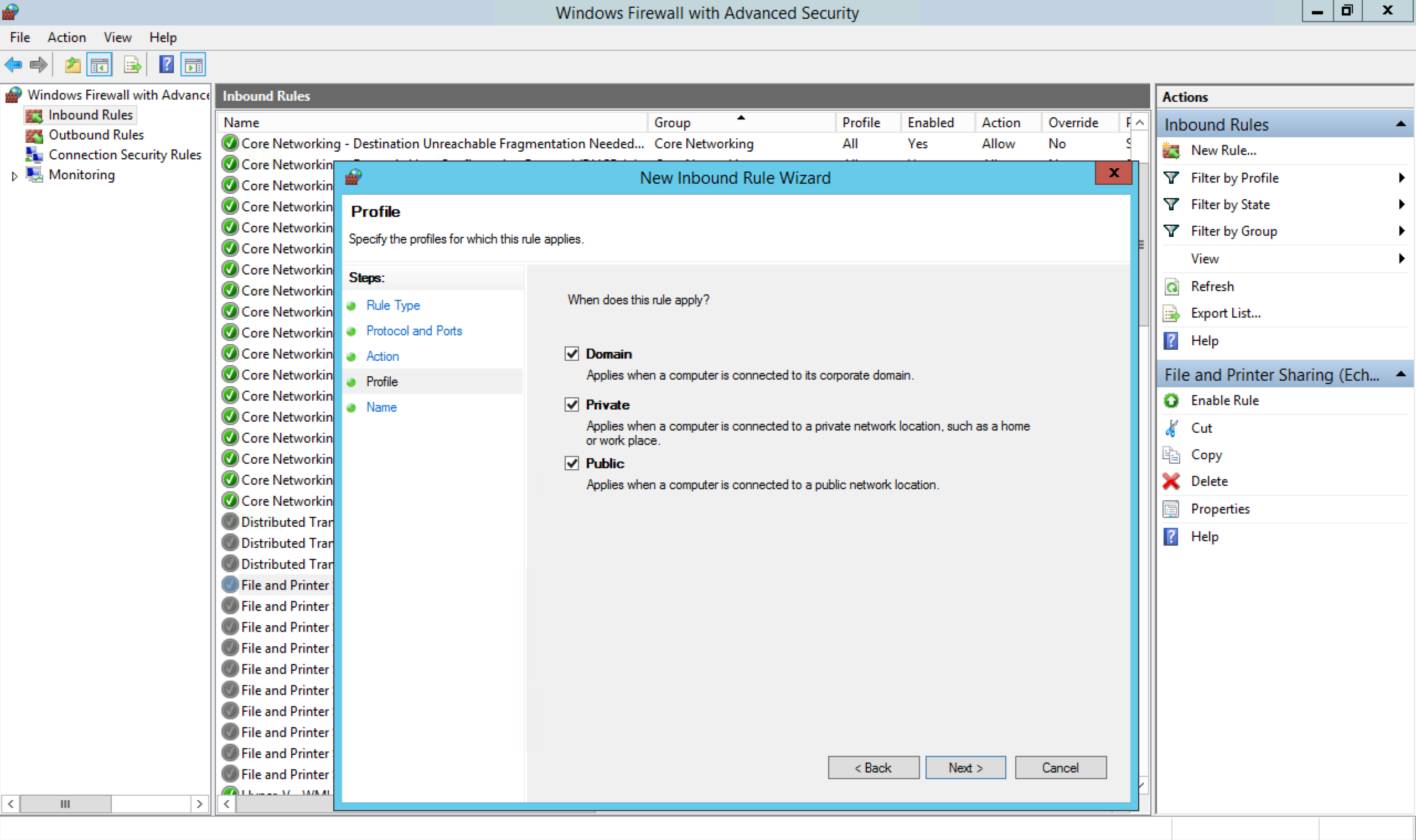
On the host, open the Windows Firewall with Advanced Security program.
Select Inbound Rules, and navigate to the Remote Service Management (NP-In) rule.
Proceed to the Setting up the Hypervisor Connection section of this article. If the setup fails, follow the steps in the Enabling and configuring winrm and Windows Firewall section.
To set up an HTTPS connection, the Hyper-V host must have a valid certificate for the WinRM service before the connection to the SIRIS device is added. The certificate must be signed by a certificate authority that is trusted by most any computer.
To configure the WinRM service to use a valid, signed certificate that is in the .p12 format:
On the Hyper-V host, launch Powershell as admin.
Modify this script to set the values for "$certPath" and "$hostname". "$certPath" should be the location of the .p12 file. "$hostname" should be the common name from the certificate.
$certPath = "C:\path\to\the\certificate.p12"
$hostname = "commonNameOfCert"
# Import the certificate file into the Certificate Store
Import-PfxCertificate -FilePath $certPath -CertStoreLocation Cert:\LocalMachine\My
# Create the WinRM listener that uses that certificate
$cert = Get-ChildItem -Path Cert:\LocalMachine\My | Where-Object { $_.Subject -match "$($hostname)"}
winrm create winrm/config/Listener?Address=*+Transport=HTTPS "@{Hostname=`"$($hostname)`";CertificateThumbprint=`"$($cert.ThumbPrint)`"}"NOTE When you add the connection on the Siris, for the "Server Address" field, you must use the hostname that matches the comman name of the certificate; the IP address will not work.
Execute the script.
IMPORTANT Run the following commands directly on the host. You must use an elevated command prompt as they will not run properly in Windows PowerShell.
Setting up and configuring Hyper-V requires local administrator rights. To set up Hyper-V as a domain account, follow this procedure, simulating local admin permissions.
From an elevated Command Prompt session, run the
winrm quickconfigcommand to enable remote management.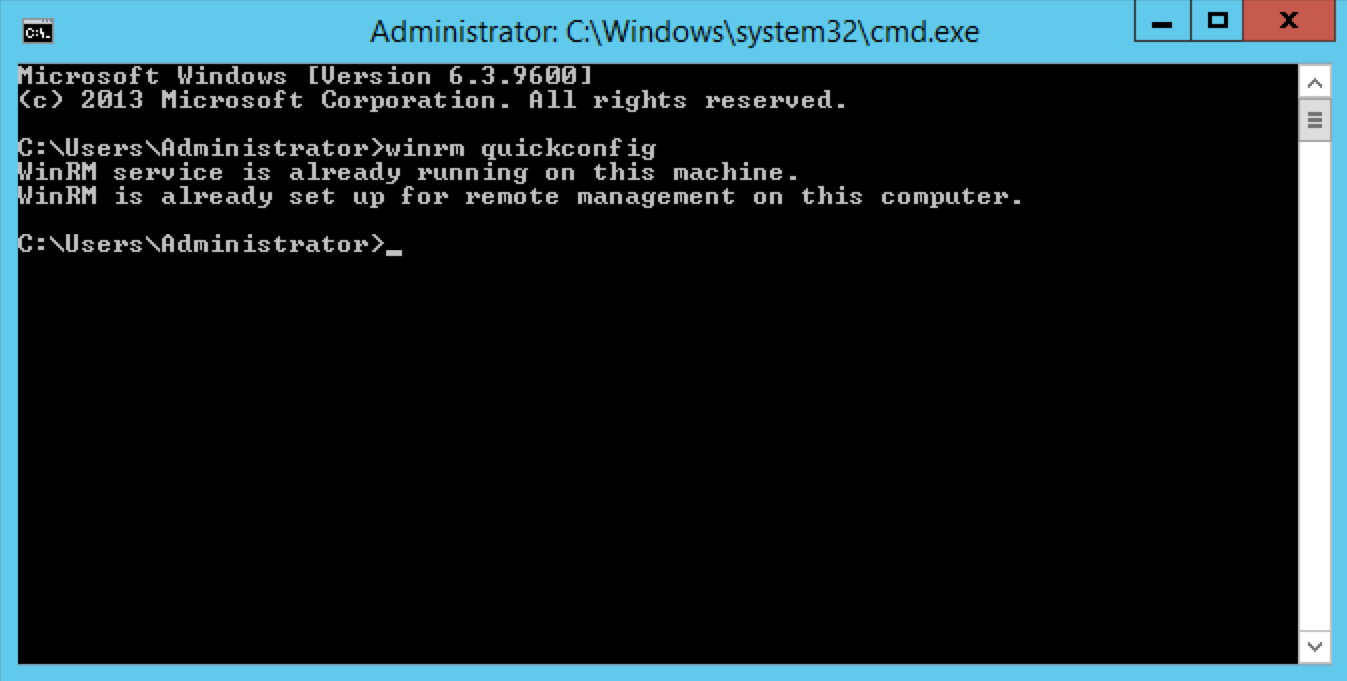
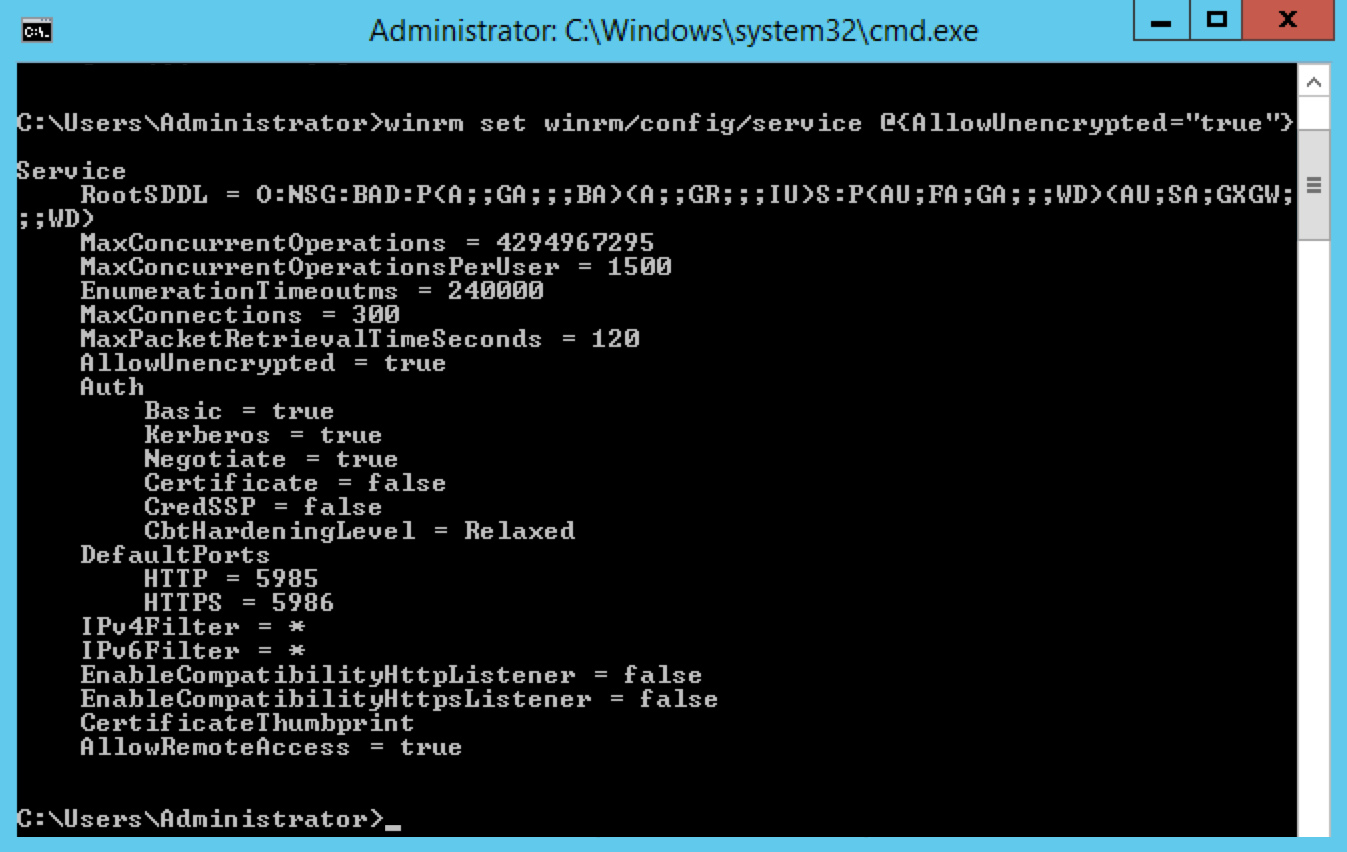
Enable basic authentication:
winrm set winrm/config/service/auth @{Basic="true"}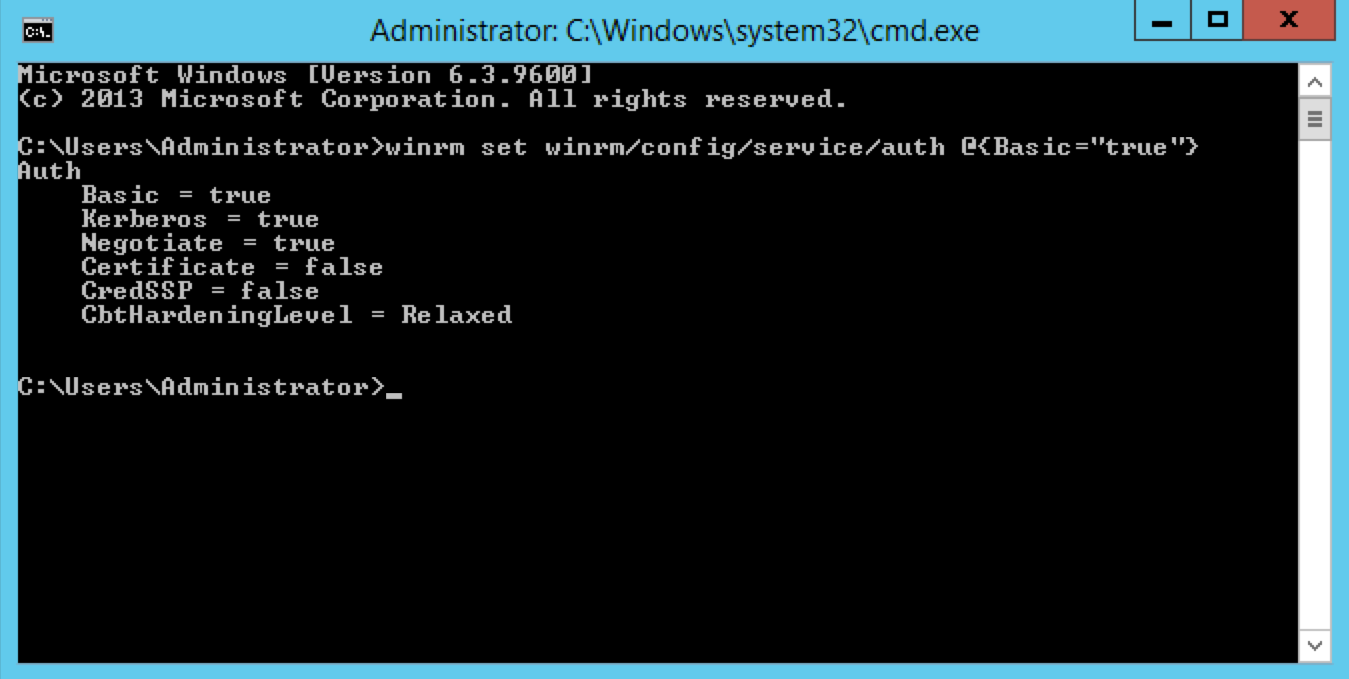
Enable transfer of unencrypted data on the WinRM service:
IMPORTANT Enabling this feature will allow the transmission of authentication information over HTTP. If you are connecting with HTTPS, this step may be skipped.
winrm set winrm/config/service @{AllowUnencrypted="true"}
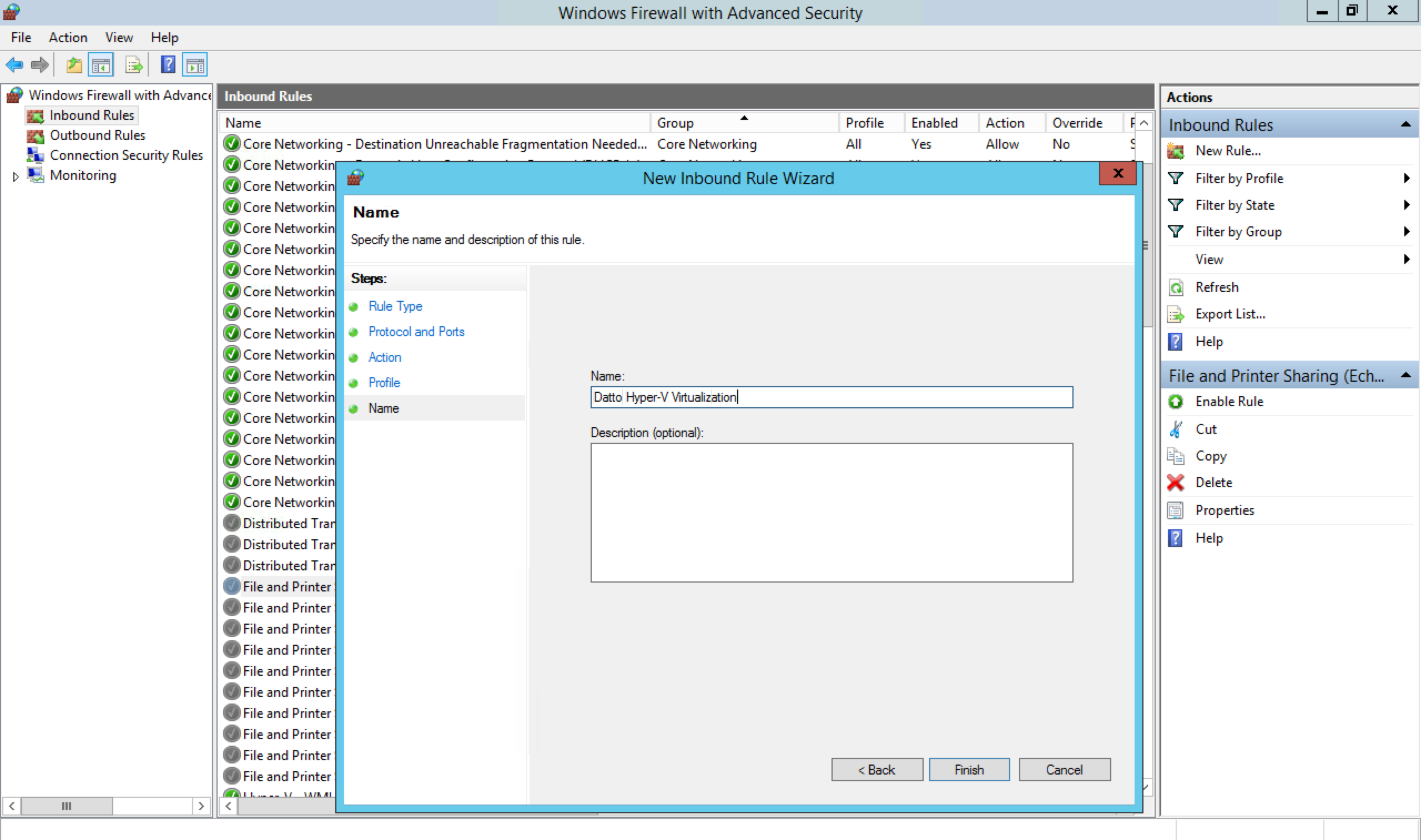
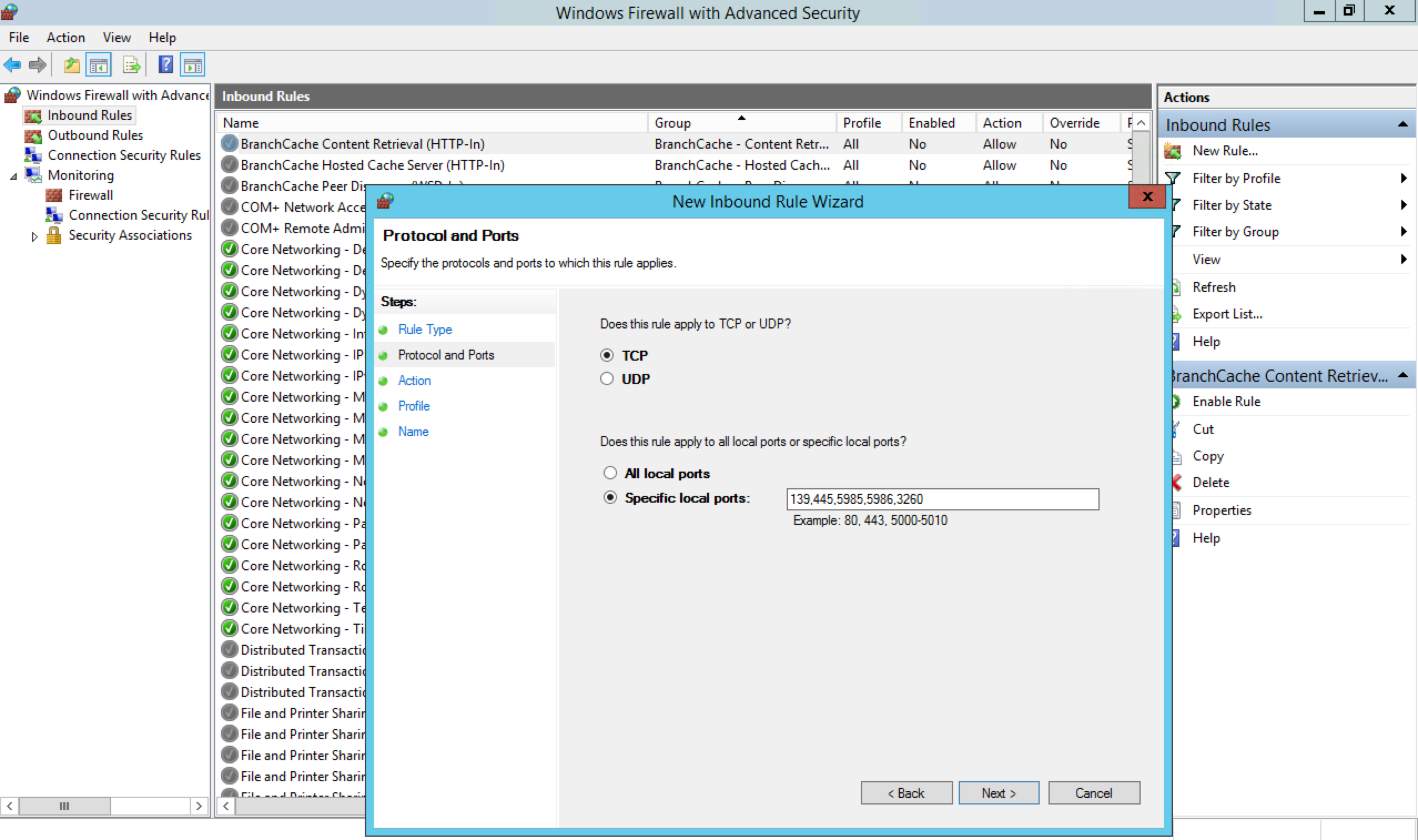
Create a new Inbound rule to allow TCP ports 139, 445, 5985, 5986, and 3260 through the Windows Firewall. These ports are for Samba, WinRM, and iSCSI.
Launch the Windows Firewall with Advanced Security control panel, and select Inbound Rules > New Rule. In the New Inbound Rule Wizard, select Port and click Next.
Select TCP, and then select Specific local ports. Specify ports 139, 445, 5985, 5986, and 3260 for the forwarding rule, and click Next.
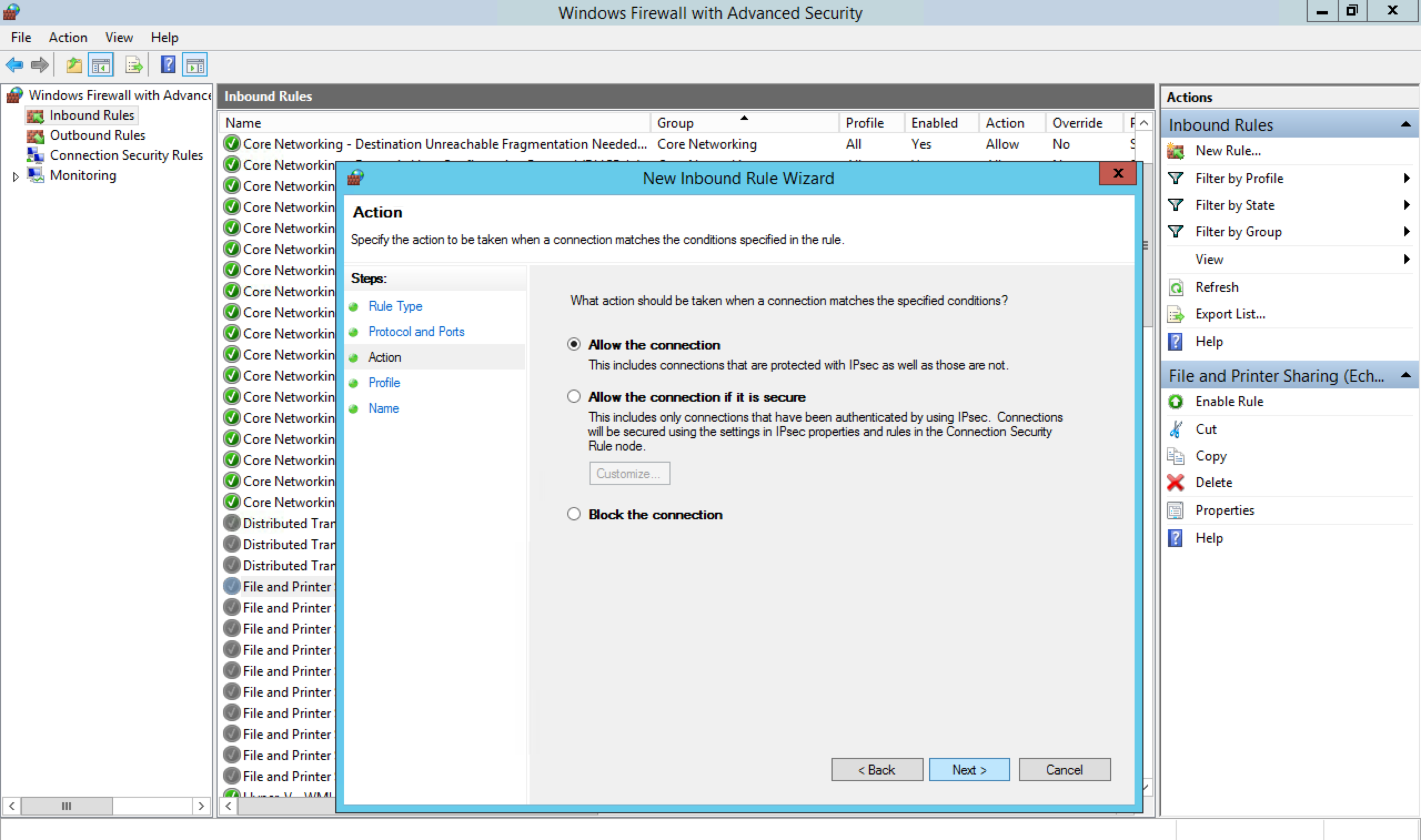
Select Allow the connection on the Action tab, and click Next.
Select Domain, Private, and Public on the Profile tab, and click Next.
Problem
When running the winrm quickconfig -q command, you receive output similar to the following:
C:\Users\ottad>winrm quickconfig -q
WinRM service is already running on this machine.
WinRM is not set up to allow remote access to this machine for management.
The following changes must be made:
Configure LocalAccountTokenFilterPolicy to grant administrative rights remotely to local users.
WSManFault
Message = Access is denied.
Error number: -2147024891 0x80070005
Access is denied.
Solution
According to Microsoft, local Administrator accounts other than the built-in Administrator account may not have the rights to manage a server remotely, even if the production machine has remote management enabled.
You will need to configure the Remote User Account Control (UAC) LocalAccountTokenFilterPolicy registry setting to allow local Administrator accounts to manage the server remotely.
To disable these restrictions, follow the below steps.
IMPORTANT You may need to reboot the production machine for these changes to take effect.
- In the Windows Registry, navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System, and change the value of the LocalAccountTokenFilterPolicy key to 1.
- If the LocalAccountTokenFilterPolicy entry does not exist, create a new DWORD Value called LocalAccountTokenFilterPolicy. Change the key's value to 1.
Problem
You are unable to add a Hyper-V connection to the Datto appliance using domain credentials, but you can add it without issue using local credentials.
Solution
This issue indicates that the domain administrator account does not have the correct permissions to manage Hyper-V hosts with Hyper-V Manager remotely. See Remotely manage Hyper-V hosts with Hyper-V Manager(external link) for information about configuring a domain administrator account with Remote Management permissions.
Setting up the Hypervisor Connection
Access the GUI of your SIRIS over your LAN or through a Remote Web connection.
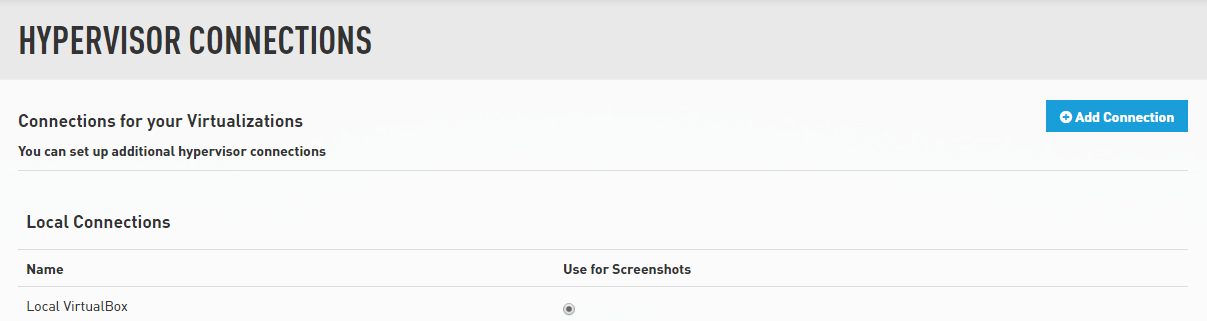
From the Datto appliance's Overview page, click Configure> Hypervisor Connections.
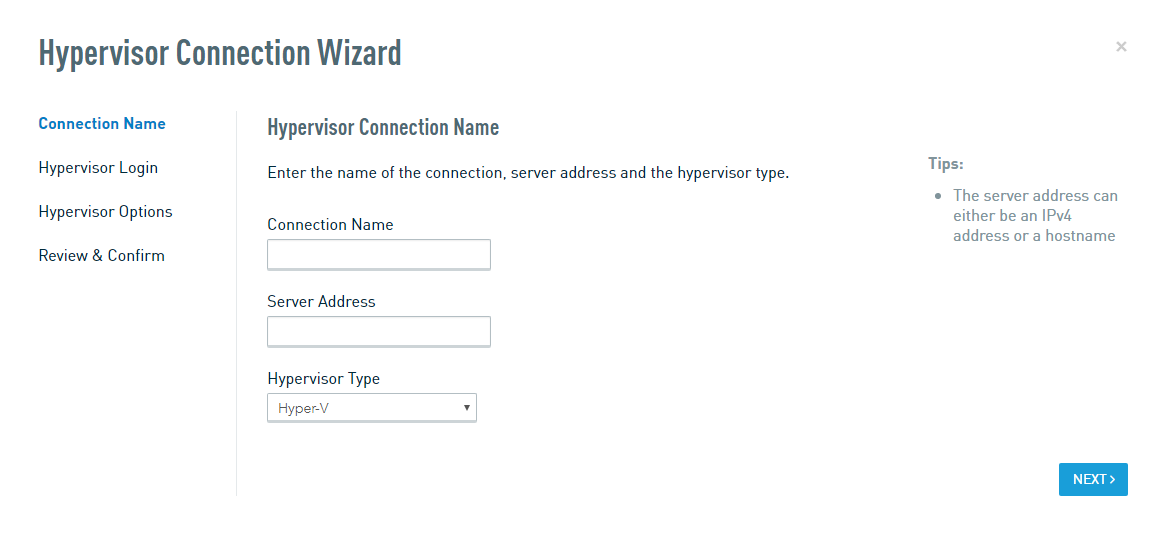
Enter a unique name for the new hypervisor connection, and the IP address, hostname, or FQDN of the Hyper-V host that the Datto appliance needs to connect to. Select Hyper-V from the Hypervisor Type menu.
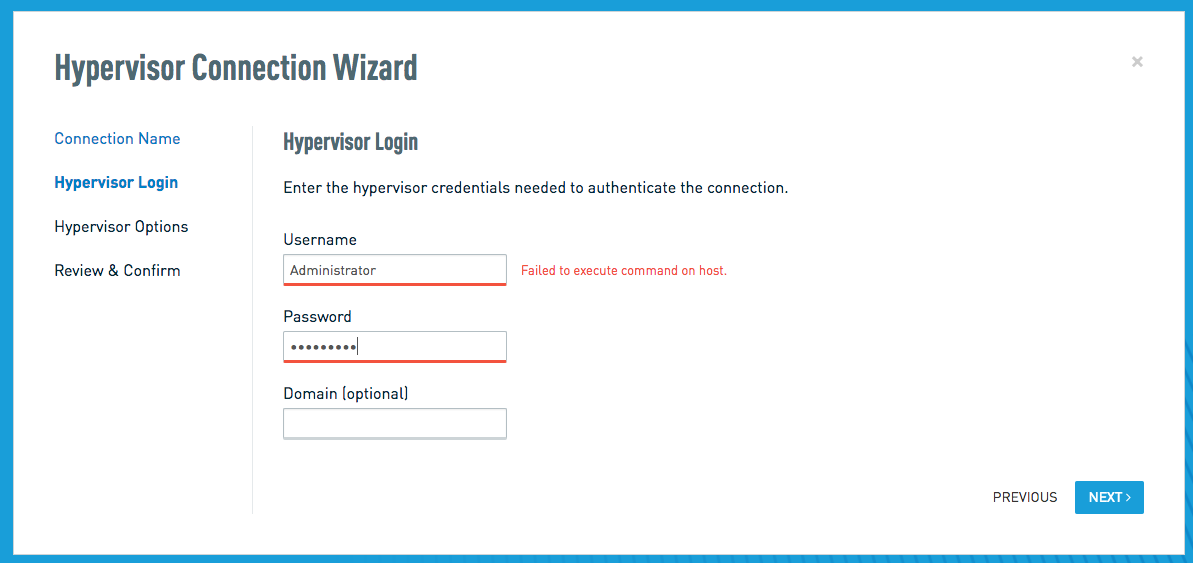
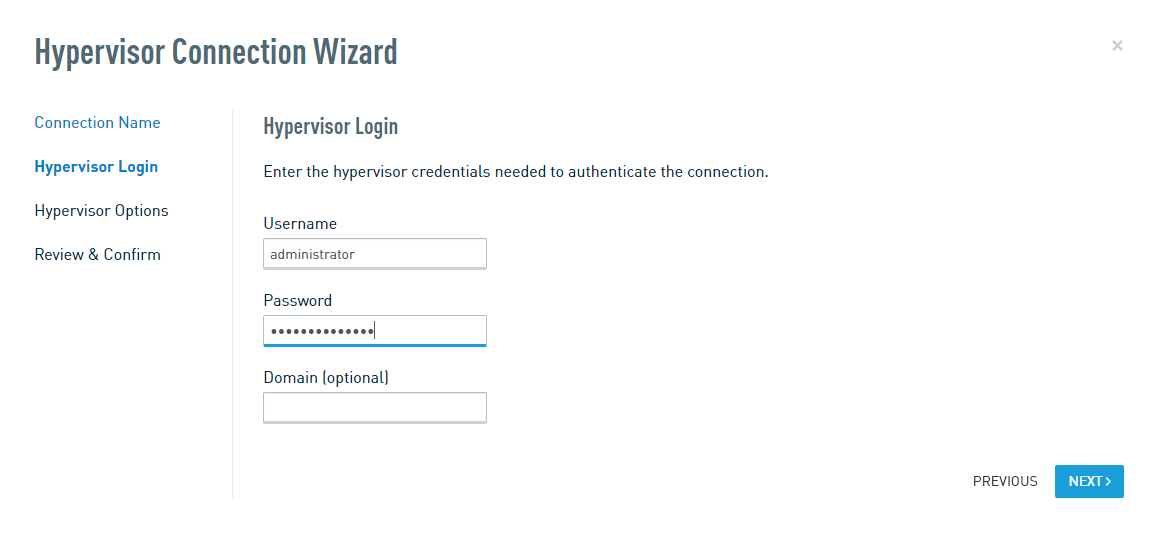
On the Hypervisor Login tab, enter the credentials for a user that has the appropriate permissions to configure and control Hyper-V on your host. You will need the username and password, as well as the domain for the user (if applicable).
NOTE If you receive an error message stating "Failed to execute command on host," review the Technical Notes section of this article to ensure that your Hyper-V configuration meets the specified requirements.
If the wizard does not report any errors, click Finish to exit the Hypervisor Connection wizard.
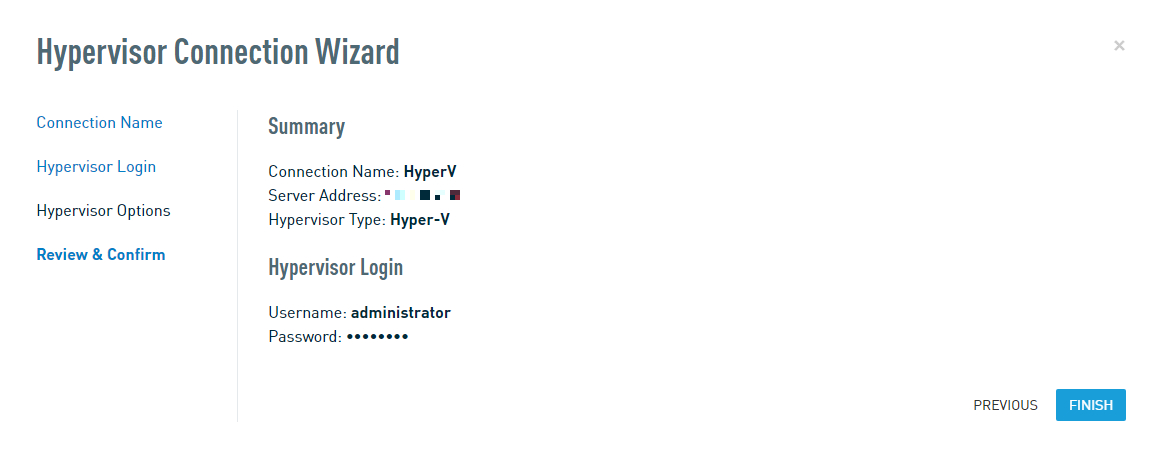
The Datto appliance will return you to the Hypervisor Connections screen, where you will see the newly-added connection listed in the HyperV Connections pane. Click the radio button under Use for Screenshots if you would like the agent to use the resources of your hypervisor during screenshot verification.
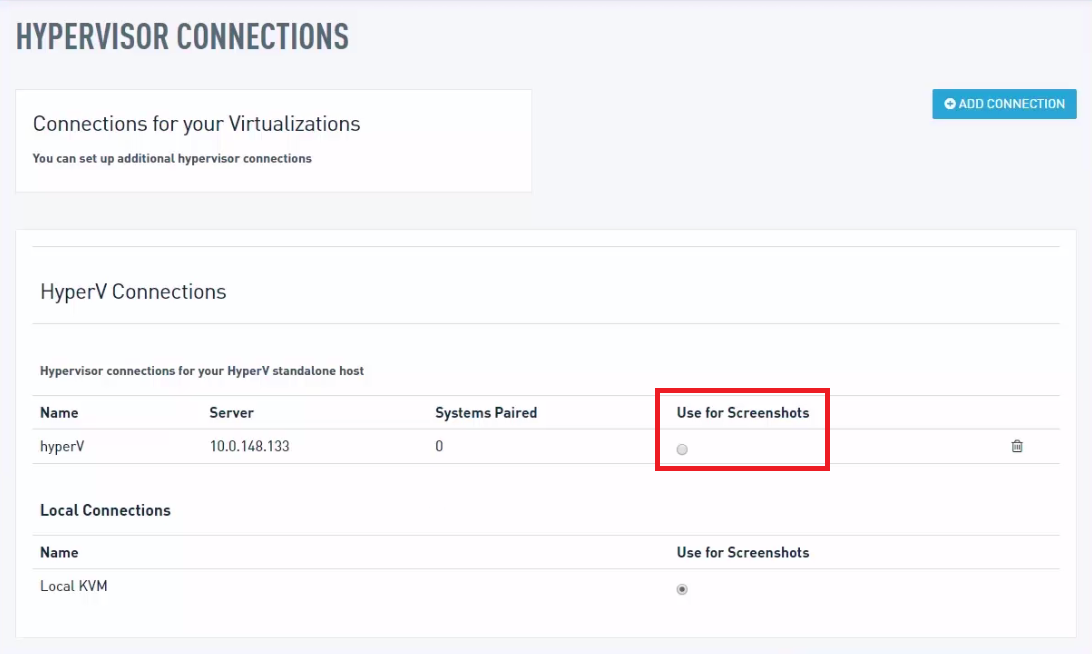
NOTE Advanced Backup Verification features of the screenshots do not function on hyperV virtual machines, as it does not support the necessary tools to run the verification.
If you need to update the hypervisor credentials for an existing connection, delete the old one, and then replace it using the *original* connection name and the new credentials. You will not lose data.
If the password for the account used to create the connection changes, you will need to edit the hypervisor connection on the Datto to use the new password.
Additional Resources
- Understanding and troubleshooting WinRM connection and authentication (external link)
- Test-WSMan: Tests whether the WinRM service is running on a local or remote computer (external link)
- Powershell Remoting (external link)