Unified Backup Networking and Bandwidth Requirements
This article describes local and off-site networking requirements and best practices for Unified Backup appliances and the Datto Endpoint Backup solution.
NOTE As of January 3, 2017, Datto appliances no longer support SNMP.
Environment
- Datto SIRIS
- Datto ALTO
- Datto NAS
- Datto Endpoint Backup
Description
- Network link speed requirements
- Network architecture considerations
- WAN uplink considerations
- Network MTU considerations
- Port access and IP allowlist requirements
- Internet access requirements
- IPMI considerations
- Virtual SIRIS considerations
- Samba considerations
- Additional Resources
By default, Datto disables local network access to the Datto device UI. You can enable local access under Configuration > Global Device Settings > Local Access Control in the Datto Remote Web UI.
Network link speed requirements
A 100 Mbps network cannot efficiently transfer large datasets between the protected machines and a Datto appliance. A gigabit network connection is reccomended between all protected machines and the Datto appliance over the LAN. All SIRIS 3, 4, and 5 devices (as well as the ALTO and NAS devices in these lines, with the exception of DN-3A) must use a gigabit connection. They will not function on a slower connection.
Datto strongly recommends placing the Datto appliance and all protected machines on the same LAN. If you must set up backups over a WAN, a 50 Mbps dedicated uplink is needed for every terabyte of protected data. Otherwise, backups will not be reliable. Even if you meet this requirement, the latency between endpoints will significantly decrease backup throughput. The higher the latency, the lower the performance.
Any device function performed through a site to site VPN/MPLS will be subject to degraded performance.
Network architecture considerations
Datto expects that you will deploy BCDR appliances in a secure LAN environment. Inbound access from untrusted WAN hosts should be blocked at the edge of the network (via the router/firewall) to limit the accessibility of appliance network daemons and services. For more information, see Secure Deployment Best Practices For Datto Appliances.
WAN uplink considerations
To reliably synchronize with the Datto Cloud, ensure that your connection is at least 1 Mbps (125 KBps) uplink per terabyte of protected data stored locally on the Datto device. To check how much data your Datto appliance is currently protecting, see this article. While the rate of change of a protected machine is largely influenced by the total volume, there are other factors that can effect it.
For every 1 Mbps of upload capacity that you dedicate to off-site traffic, you will be able to upload approximately 10 GB of change per day.
Examples
- 2 Mbps of upload capacity would net approximately 20 GB of change uploaded per day.
- 10 Mbps of upload capacity would net approximately 100 GB of change uploaded per day.
- 100 Mbps of upload capacity would net approximately 1 TB of change uploaded per day.
Viewing the ideal case daily sync transfer amount, as well as the current system's rate of change, can be done on the Off-Site Synchronization Configuration page.
Offsiting 1 TB of change over a 1 Mbps uplink will take approximately 100 days. For images this large, Datto recommends using the RoundTrip service to send the original base image offsite.
Network MTU considerations
The Datto appliance will most reliably communicate with our monitoring servers when you set the router's MTU size to 1500 bytes. Since the Datto appliance is also using a 1500 byte MTU size, this will prevent packet fragmentation, which can cause issues with communication to our monitoring servers.
Port access and IP allowlist requirements
Ports 25566 and 25568 (listed as 6001-47000 when WinNAT is enabled) must be open.
Depending on your network security configuration, you may need to allow-list python.map.fastly.net for optimal device communication. Additionally, all protected machines must be able to resolve mothership.dtc.datto.com, agent-update.datto.com, and dattolocal.net in the local DNS.
Additional port access requirements will vary, depending on the type of agent deployed. See the specific agent documentation linked below for more information.
You may need to contact your ISP if they throttle port 22 or SSH traffic, as this may cause performance issues with synchronization.
Firewall considerations
Many next-generation firewalls and unified threat management (UTM) platforms include threat detection technology which can interrupt or interfere with cloud synchronization. These vary by vendor, and may require additional adjustments. See Datto Appliances and firewalls for more information.
For networking requirements specific to Datto's various agent and agentless backup solutions, see the following articles:
Getting started with the Datto Windows Agent
- Gigabit connections from the Datto appliance to all appropriate network infrastructure. For best results, the Datto appliance should be connected to a gigabit switch whenever possible.
- The protected machine must have Internet access and be able to reach https://device.dattobackup.com/certApi.php for the initial installation and ongoing operation of the Datto Windows Agent.
- Outbound connectivity on the protected machine:
- Port 443 (for Datto Cloud communication)
- Port 3260 (for iSCSI)
- Port 3262 (for MercuryFTP)
- Inbound connectivity on the protected machine:
- TCP port 25568 (for Datto Windows Agent service)
- Outbound from the Datto appliance to the Internet:
- Ports 22, 80, 123, 443
- Bypass any local proxy to 8.34.176.9 (webserver.dattobackup.com), on port 443 for correct certificate installation during DWA install.
- The protected machine must be able to reach http://cacerts.digicert.com and ocsp.digicert.com for certificate authentication
- All protected machines must be able to resolve dattolocal.net in the local DNS.
- The Datto Windows Agent uses MercuryFTP as its primary transport method; however, if this method fails, backups are intended to fall back to iSCSI.
Getting started with the Datto Linux Agent
- Gigabit connections from the Datto appliance to all appropriate network infrastructure. For best results, the Datto appliance should be connected to a gigabit switch whenever possible.
- The protected machine must have Internet access and be able to reach the following for the initial installation and ongoing operation of the Datto Linux Agent.
- https://device.dattobackup.com/certApi.php
- https://cpkg.datto.com
- Outbound connectivity on the protected machine:
- Port 443 (for Datto Cloud communication)
- Port 3260 (for iSCSI)
- Port 3262 (for MercuryFTP)
- Inbound connectivity on the protected machine:
- TCP port 25567 (for Datto Linux Agent service)
- Outbound from the Datto appliance to the Internet:
- Ports 22, 80, 123, 443
- All protected machines must be able to resolve dattolocal.net in the local DNS.
Getting started with agentless backups
Communication between the virtual environment and the Datto appliance requires the following ports open for inbound and outbound traffic:
On both the Host and the Datto Appliance:
- TCP 443 (HTTPS)
- TCP 902 (Network File Copy)
On the Datto Appliance:
- TCP 10443 (HTTPS)
- TCP 9000-9010 (Failover ports)
- TCP 3260 (iSCSI)
- TCP/UDP 111 (NFS)
- TCP/UDP 2049 (NFS)
- TCP 22 (SSH)
- TCP 9080 (IO Filter)
- TCP 8805
Internet access requirements
- The Datto appliance must have access to the Datto Cloud for backup replication and remote device management. Also, all ICMP packets must be allowed through the firewall.
- Datto recommends disabling any application-layer filtering of traffic destined for or originating from your Datto appliance.
For device management, to synchronize time, and to download operating system updates, all backup appliances must be able to resolve the following Datto sites in the local DNS:
- dattobackup.com
- dattoweb.com
- datto.com
- device-packages.dattobackup.com
- device-images.datto.com
- ntp.dattobackup.com
- dlt-rly-*.datto.com
- fra-rly-*.datto.com
- syd-rly-*.datto.com
NOTE (* is a wild card; these domains will continue to expand)
For operating system maintenance, the Datto appliance must also be able to resolve the following community sites in the local DNS:
- ntp.ubuntu.com - Ubuntu managed Network Time Portal server, used to synchronize time
- us.archive.ubuntu.com - Ubuntu managed application repository
- security.ubuntu.com - Ubuntu managed application repository
- ppa.launchpad.net - Ubuntu managed application repository
Access to an NTP server is required for virtualizations to synchronize to the correct time zone. When a Windows VM lacks access to an NTP server, the Windows Time Service will synchronize to the hardware clock. For cloud VMs, this will mean that they set their time zone to UTC.
In addition to the partner portal (dattobackup.com) users must be able to reach the following in order to configure 2fa and display the QR code image.
- api.qrserver.com
Cloud infrastructure, DNS failback, and device management
All Datto appliances must have outbound access to the following IP ranges for Cloud infrastructure, DNS failback, and device management.
Ensure your firewall/security appliance allows bidirectional communication on port 443/TCP to these IP ranges. Some enterprise firewalls may require additional configuration for API connections, such as:
- Extended connection timeouts for HTTPS sessions
- Disabling deep packet inspection for these destinations
- Allowing long-running API transactions
| IP Range | Ports | UDP/TCP | Purpose |
|---|---|---|---|
| 8.8.8.8 1.1.1.1 1.0.0.1 | 53 | Both | DNS |
| 206.201.138.10 206.201.138.11 206.201.138.15 206.201.138.20 | 123 | UDP | NTP |
| 206.201.138.36 | 80, 443 | TCP | SupportTools |
| 8.34.176.0/23 172.64.148.147* 104.18.39.109* | 443 | TCP | Datto Portal |
| 162.244.87.51 | 443 | TCP | Cloud restores |
| 162.244.85.60 | 443 | TCP | Image / package server |
| 162.244.87.0/24 198.137.225.0/24 | 443, 80 | TCP | Remote Web |
| 198.49.95.0/24 | 21 | TCP | Bandwidth testing |
| North America: 206.201.136.0/24 EMEA: 185.217.57.0/24 Asia Pacific: 103.109.129.0/24 203.22.186.0/24 | 80, 443, and 2200-2250 | TCP | Remote Web and cloud storage |
NOTE * These IPs are controlled by Cloudflare and are subject to change. You may find you need to whitelist additional IPs from within the list at Cloudflare IP Range. If you see the device communicating with IPs in this range that are not listed and have concerns, reach out to Datto Support.
Hybrid virtualizations, VPN tunneling, and off-site storage
The Datto appliance must have outbound access to port 22 (TCP) for data synchronization and ports 1194-65535 (TCP/UDP ) for hybrid virtualizations, VPN tunneling, and off-site storage.
Other machines attempting to connect to an offsite virtualization via VNC will also need to be able to reach the offsite server hosts' IP using port 9443 (TCP).
United States
- 8.34.165.0/24 (Pennsylvania)
- 8.34.176.0/24 (Pennsylvania)
- 8.34.177.0/24 (Pennsylvania)
- 8.34.181.0/24 (Pennsylvania)
- 161.129.211.0/24 (Pennsylvania)
- 161.129.215.0/24 (Pennsylvania)
- 161.129.217.0/24 (Pennsylvania)
- 161.129.218.0/24 (Pennsylvania)
- 161.129.222.0/24 (Pennsylvania)
- 162.142.95.0/24 (Pennsylvania)
- 162.244.84.0/24 (Pennsylvania)
- 162.244.85.0/24 (Pennsylvania)
- 192.171.101.0/24 (Pennsylvania)
- 192.171.103.0/24 (Pennsylvania)
- 198.49.95.0/24 (Pennsylvania)
- 198.137.226.0/24 (Pennsylvania)
- 206.201.136.0/23 (Pennsylvania)
- 161.129.209.0/24 (Utah)
- 161.129.216.0/24 (Utah)
- 198.137.225.0/24 (Utah)
- 206.201.133.0/24 (Utah)
- 208.53.34.0/23 (Utah)
- 208.53.53.0/24 (Utah)
Canada
- 198.137.227.0/24 (Montreal)
- 161.129.210.0/24 (Montreal)
- 161.129.219.0/24 (Toronto)
- 161.129.223.0/24 (Toronto)
- 192.171.102.0/24 (Toronto)
- 206.201.134.0/24 (Toronto)
EMEA
- 185.147.180.0/24 (UK)
- 185.147.181.0/24 (UK)
- 185.217.56.0/24 (UK)
- 185.252.164.0/24 (UK)
- 139.28.147.0/24 (Iceland)
- 185.217.58.0/24 (Iceland)
- 185.252.165.0/24 (Iceland)
- 139.28.146.0/24 (Germany)
- 185.217.57.0/24 (Germany)
- 185.217.59.0/24 (Germany)
- 198.137.225.0/24 (Germany)
ANZ (Australia and New Zealand)
- 103.109.129.0/24 (Sydney, Australia)
- 203.22.186.0/24 (Sydney, Australia)
- 203.23.127.0/24 (Sydney, Australia)
- 103.109.130.0/24 (Melbourne, Australia)
Singapore
- 103.109.128.0/24
NOTE It is normal to see the Datto appliance repeatedly connecting to one or more of the IP addresses listed above as it checks in with our monitoring servers.
To learn which Cloud storage node a Datto device uses, log into the backup appliance's GUI. The replication information will be available on the Home page similar to the example below: 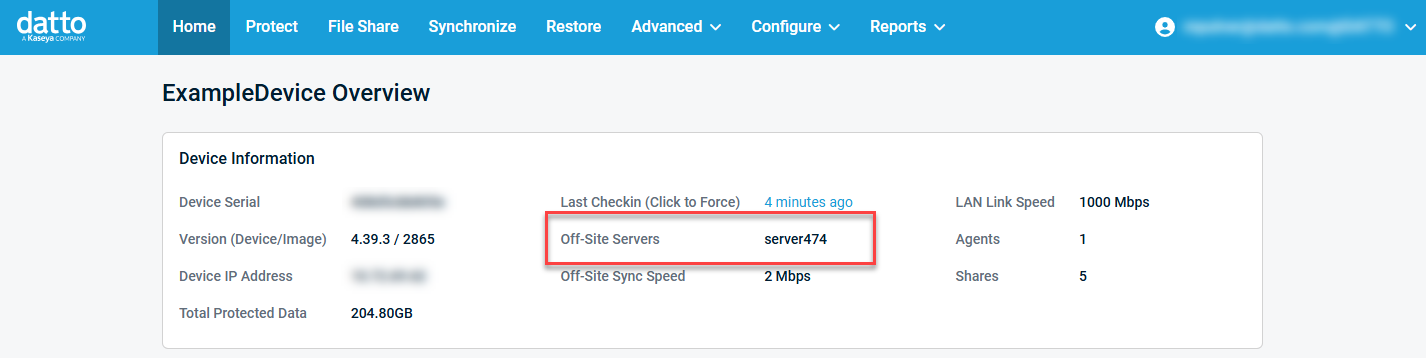
IPMI considerations
NOTE Datto strongly recommends enabling IPMI on Datto appliances that include this feature and configuring the IPMI port with a static IPv4 address. Enabling IPMI will allow you to access the device for remote troubleshooting if you cannot access the GUI.
IPMI access requires the local network to be within a private IP range (10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16) per IANA standards (external link).
Virtual SIRIS considerations
When performing an off-site hybrid virtualization on a virtual device bridged to your local network, ensure you have enabled promiscuous mode and forged transmits on the port group or virtual switch to which the vSIRIS is connected.
Port 8805 must remain open for Datto to communicate with the Hypervisor.
Samba considerations
To use the NAS Guard feature to back up a hosted share on the network, the Datto device will need to be able to reach outbound over TCP port 445 (samba) to the host server. It will do this for initial pairing and on each backup request.
For hosted Samba shares, TCP 445 is required to be open from the connecting machine to the Datto device, as well as for some environments; TCP 139 for NetBIOS Session Service.